What protocol does
protocol is a turn-key automation solution which digitalises regulatory compliance processes and reviews, recording the associated data in a smart, coherent and fully auditable way.
It supports multi-jurisdiction and multi-office businesses as standard.
The system is built around powerful pre-configured workflows which are industry proven, yet adaptable to the specifics of your organisation.
Available in modular packages with protocol Core as its foundation, the system comprises:
protocol Core
- Suspicious Activity Reporting
- Regulatory Communications
- Breach and Error Reporting
- PEP Acceptance
- Adverse Screening Hit Processing
- Complaint Handling
- Exceptions
- Watchlist
- Claims and Litigation
- Conflicts of Interest
- Gifts and Hospitality
- Advertising
protocol Core+
- Periodic Reviews
- Customer Risk Assessments (“CRA“)
- PEP Reviews
- 90 Day Reviews
- Compliance Monitoring
- Action Point Creation & Management
- Business Risk Assessments (“BRA”)
protocol CDD
- CDD pack collation
- Electronic identity (“eID“) and address verification
- Internal review, approval and acceptance
- Trigger event review
- Verification document inventory management
- Dynamic structure chart generation
protocol New Business
- Acceptance and onboarding of new clients
- Interacts dynamically with CRA and CDD modules
- Pre-designed forms based on industry best practice
- Customisable process to fit your operating model
- Integrates with administration/primary business platform via API
protocol Core
Manages a dozen principal risk, compliance and AML processes which are regulatory non-negotiables:
- Suspicious Activity reporting, PEP Acceptance, Conflicts of Interest, Complaints, Breaches, Regulatory Communications plus more.
- Data is captured immediately when the user initiates and completes a form and updated at subsequent steps as the matter is dealt with.
- Provides real-time senior level visibility over the reportable and regulatory activity within any regulated or supervised entity across multiple jurisdictions.
- Ensures the application of first line compliance responsibilities and evidences user involvement and accountability.
- Every process is accompanied by deep data dashboards and automatically updated registers.
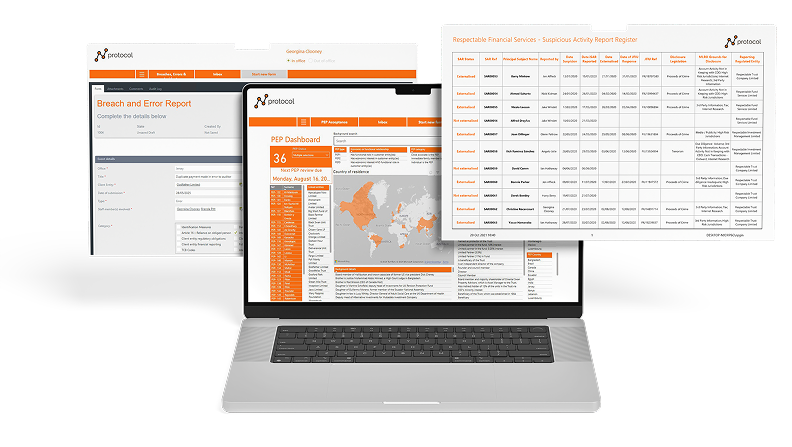

protocol Core+
Our powerful review, risk assessment and action points module:
- Author, schedule and deploy all types of periodic and compliance-related reviews into your business.
- Define, build and maintain for yourself dynamic question sets including Periodic Reviews, 90 Day Reviews, PEP Reviews, Compliance Reviews and Customer Risk Assessments.
- Run reviews at will against clients or parties and gain insights from every shred of data being reportable.
- Initiate Action Points instantly while a Review is being performed. Each Action Point is assigned automatically to the right person and is fully auditable so can be tracked to completion.
protocol CDD
Much more than just an electronic identity verification solution:
- Complete end to end management of your CDD packs and process: from creation to approval, plus CDD trigger event review, update and reapproval.
- Verification and supporting CDD documentation is included and signed off in granular detail.
- Automatically generate ownership and control structure charts which dynamically update as CDD records evolve over time.
- Get ahead of trigger event CDD reviews by knowing in advance which documents are expiring and when.
- Perform a CDD update review without needing to pick up a physical pack again.
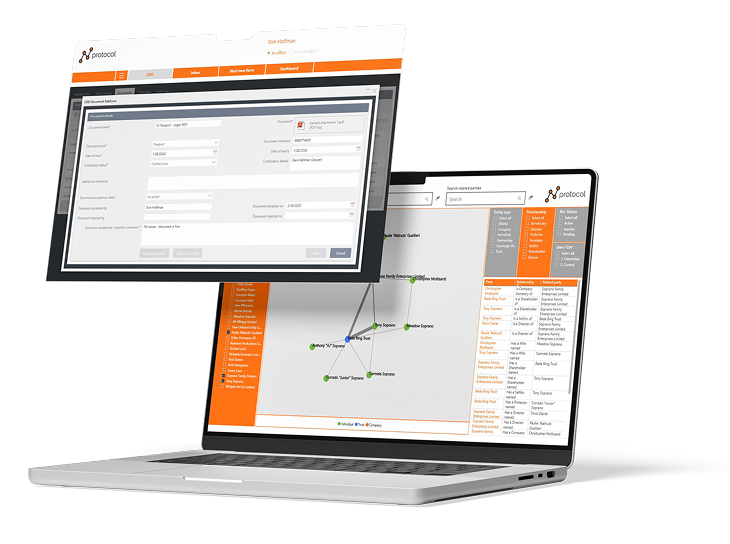
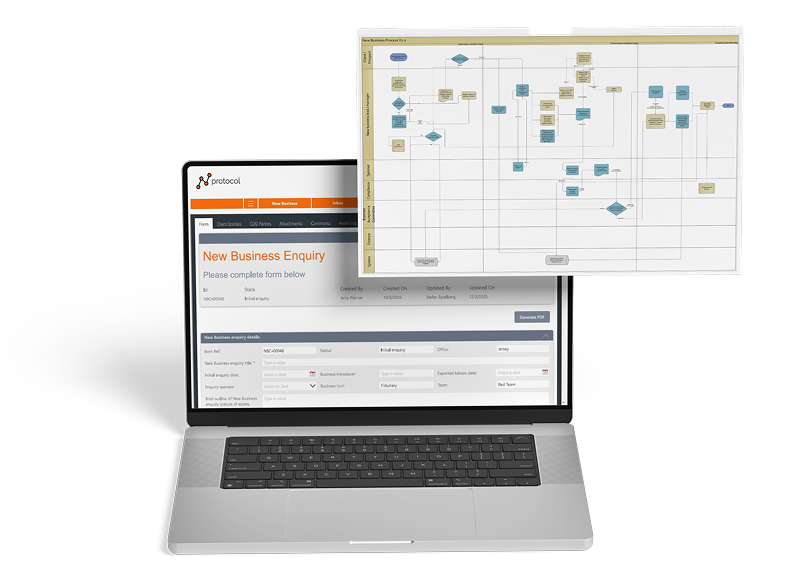
protocol New Business
Manages the internal approvals and acceptance of new clients in line with governance and regulatory expectations.
- Out of the box process developed from field tested industry experience but designed to be customised to meet the precise needs of the business.
- Combines with the protocol CDD module to record and approve parties connected to the new business enquiry, so onboarding into BAU is smooth and integrated.
- Interacts with the CRA module from protocol Core+ to create initial take-on and subsequent, post-acceptance BAU risk assessments.
- Integrates with primary administration or client management platforms via API to create client or party records in the core admin system.
- Features all the other benefits of the protocol approach, including real-time visibility of new business applications and their progress, full audit trail, data driven insights and regulatory outputs such as Declined Business Register.
FAQs
Which staff use protocol?
protocol is a first line risk and compliance application so all staff are typically provided user access to initiate and process forms. As a general rule, anyone in the client business who has AML reporting obligations ie may need to file an internal Suspicious Activity Report (“SAR”) would be a user. The advantage of all users having access is that the first line staff complete and authorise protocol forms meaning Compliance staff do not have to reinput data in registers or other reporting. It also helps clearly evidence the First Line of Defence and Second Line of Defence risk model being in operation.
How long does protocol take to implement?
protocol works ‘out of the box’ so implementation can be extremely rapid - a matter of weeks between the initial Discovery meetings to having protocol ready for User Acceptance Testing (“UAT”) if minimal changes are required. Many of our clients have chosen to adopt the forms and processes in the ‘out of the box’ version of protocol and have been able to deploy very swiftly. If significant customisations are required this will take longer but will in most cases be a matter of weeks, not months.
What does protocol come with ‘out of the box’?
protocol is deployed in modules, with 12 fundamental AML, risk and compliance processes delivered as part of protocol Core. Each of these modules includes a fully featured reporting form, defined process map, individual dashboard and regulatory required register or log report as standard. As part of the Discovery process we work through all of these elements to determine if the ‘out of the box’ solution meets your requirements or if adjustments are required. If protocol Core+ and other modules are purchased, each of the modules is delivered with similar ‘out of the box’ reporting.
Does protocol rely on the quality of your existing data?
NO! One of the most significant advantages of protocol is that it data generative. protocol is used to initiate and collect risk and compliance related data as it arises so the system is not reliant on a large existing dataset in order to work. Over time protocol becomes a hugely valuable reservoir of risk and compliance data which has all been reviewed and verified while it is processed, which means regulatory reporting, trend analysis and other data derived tasks can be fulfilled with accuracy and complete confidence.
Does protocol connect with other business systems?
Yes - protocol interacts with your core administration / CRM platform in order to make available the client and party names which may be recorded in protocol forms. This data feed is very simple to set up. protocol Core+ modules post selected data back into the core administration / CRM platform which is typically achieved using a standard Application Programming Interface (“API”) which most platforms provide. We have successfully integrated protocol with a number of different platforms (including proprietary systems).
Can we use protocol across different offices and jurisdictions?
Yes - protocol can be provided as a single system to service multiple offices. Almost all field selection options are defined by parameters in the system and these can also be tailored by Office, eg ‘Grounds for Disclosure’ of a SAR in one jurisdiction will differ to another; protocol allows both to be available so the correct jurisdiction is used depending on the Office / jurisdiction of the user. One of the major advantages for multi-jurisdictional businesses using protocol is that a group wide risk and compliance picture can be automatically presented via group dashboards and reports. This can ensure enterprise level risk and compliance reporting standards can be applied.
Where is protocol’s data stored?
protocol's data is always stored within the client’s own IT environment, whether that is on-prem servers or in the cloud. As a result, the data is always entirely under the client’s direct control and is never stored outside this area or with a third party.
Is protocol provided on premises, a cloud solution or is it SaaS?
protocol is not a SaaS product. It can be either on-prem or cloud and we have successfully deployed it in each of these settings, including subsequently migrating from on-prem to cloud. Whether the cloud is Azure or AWS, protocol can operate on it. As part of our initial Discovery we will ascertain which solution you require and provide a detailed technical requirements document which your IT team can work to; once the infrastructure is established we will take care of the rest so it is a very light touch exercise for client IT functions.
How much does protocol cost?
protocol is licensed by user numbers on an ongoing basis and we are entirely transparent on costs. There is a one-off expense which relates to Discovery, setup and installation including training and UAT support if required. Once we have determined the specific requirements we provide a comprehensive proposal which includes all cost elements, plus a detailed ROI calculation showing the value and compliance capacity gains protocol will bring to your specific business.